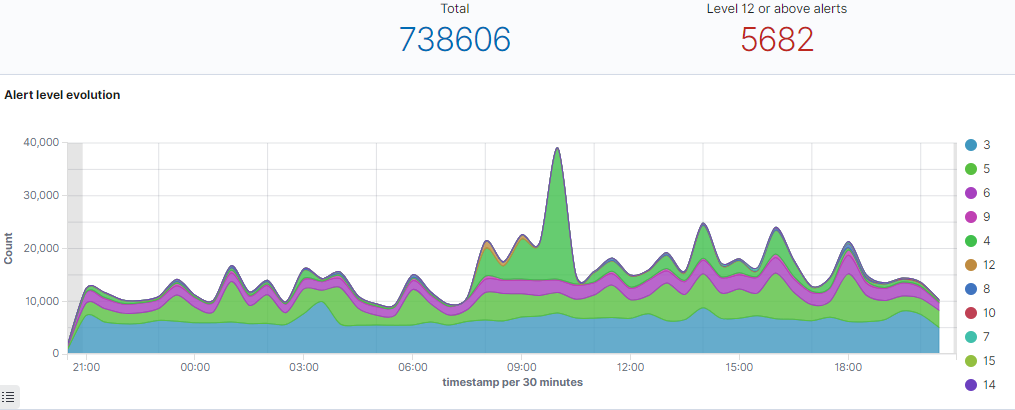
In Wazuh gibt es bereits eine Regel um fehlgeschlagene Logins zu erkennen:
<rule id="60203" level="10" frequency="$MS_FREQ" timeframe="240">
<if_matched_sid>60107</if_matched_sid>
<same_field>win.eventdata.targetUserName</same_field>
<description>Multiple failed attempts to perform a privileged operation by the same user</description>
<options>no_full_log</options>
<group>pci_dss_10.2.4,pci_dss_10.2.5,pci_dss_11.4,gdpr_IV_35.7.d,gdpr_IV_32.2,hipaa_164.312.b,nist_800_53_AU.14,nist_800_53_AC.7,nist_800_53_SI.4,tsc_CC6.1,tsc_CC6.8,tsc_CC7.2,tsc_CC7.3,</group>
<mitre>
<id>T1110</id>
</mitre>
</rule>
Allerdings basiert diese Regel auf 60107, also Failed attempt to perform a privileged operation
Eventuell interessieren uns aber Brute Force Attacken, dazu benötigen wir einen Match auf 60122:
<group name="windows,windows_security,">
<rule id="999999" level="14" frequency="5" timeframe="20">
<if_matched_sid>60122</if_matched_sid>
<same_field>win.eventdata.targetUserName</same_field>
<description>Windows: Multiple Failed Login attempts for same user.</description>
</rule>
</group>